Penetration Testing
This testing assessment uncovers vulnerabilities residing in your IT and network systems and provides a tailored approach to each environment. This service reduce the risk of a breach within the system infrastructure.
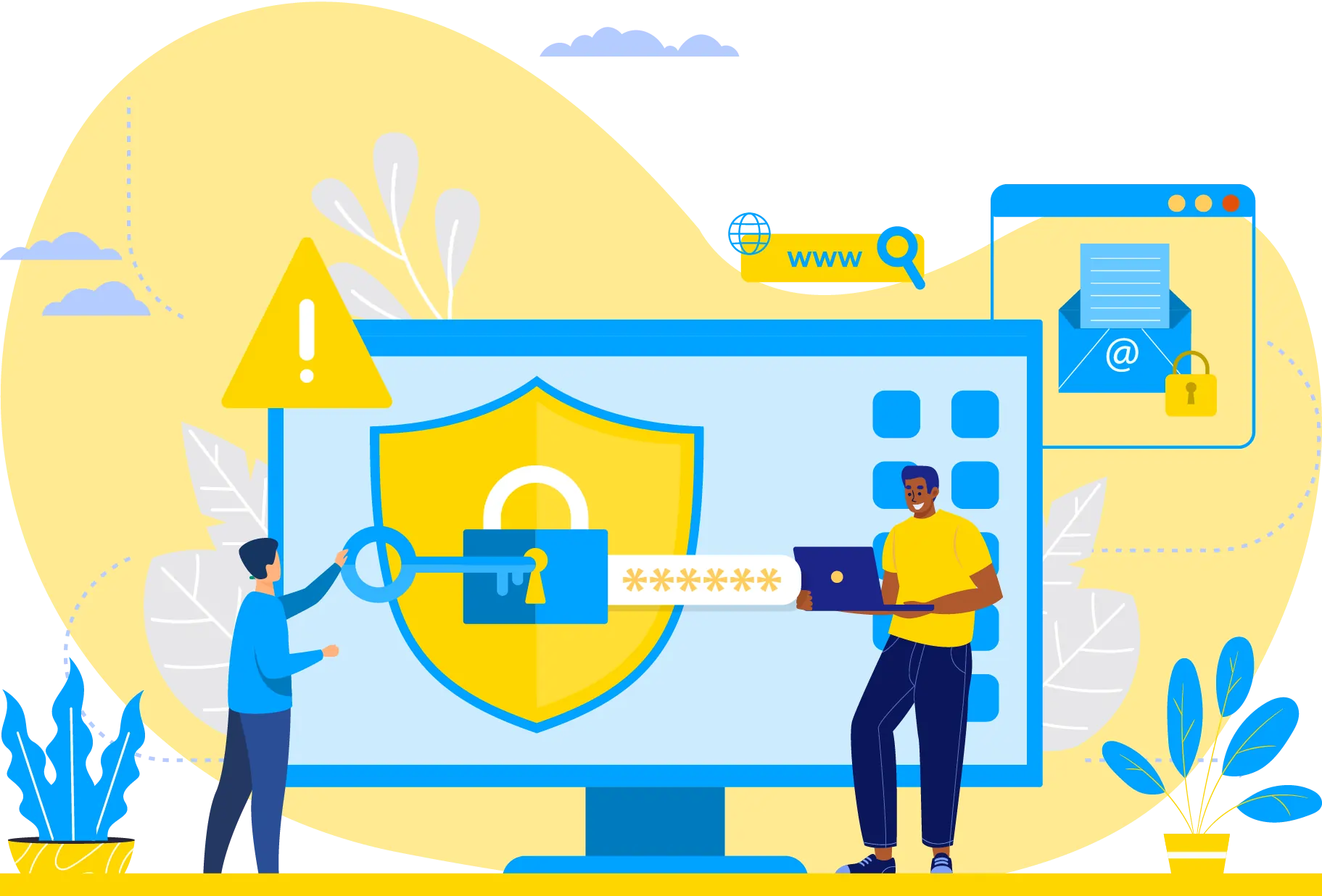
Our comprehensive cybersecurity services are designed to shield your digital world from evolving threats. We’re committed to safeguarding your data and maintaining your online security. Our expert team employs advanced techniques to detect and mitigate vulnerabilities, ensuring your systems remain resilient against cyberattacks. We offer a wide array of services, including real-time threat monitoring, penetration testing, risk assessment, and secure software development. With a focus on proactive defense, we tailor solutions to your specific needs, fortifying your infrastructure, networks, and applications. Count on us for 24/7 support, threat intelligence, and the peace of mind that comes with knowing your digital assets are in safe hands.

This testing assessment uncovers vulnerabilities residing in your IT and network systems and provides a tailored approach to each environment. This service reduce the risk of a breach within the system infrastructure.
This is an approach integrating security into the software development process. It includes automated security testing, threat modeling, and continuous monitoring, enhancing cybersecurity throughout the software development lifecycle.
Red teaming is a full scope, multi-layered simulated attack designed to get a holistic review of the level of risk and vulnerabilities across people, processes and technologies in an organization. It evaluate response to various threats.
Our cyber maturity assessment service supports the tactical direction for your cybersecurity strategy. As the first step in strengthening your security posture, this assessment generates the roadmap to strengthen your overall security program.
Cloud Penetration Testing simulates an attacker in the environment, and a Cloud Penetration Review, which provides insights into cloud-specific vulnerabilities that originate from an insecure configuration.
More targeted than traditional pen tests, application security testing detects vulnerabilities that exist in your web and mobile applications. Application security testing proactively explores your application from an attacker's perspective.
ICS/OT CyberSecurity Assessments simulate the likelihood of an attacker reaching the control center from an external and internal perspective with production-safe testing. It Identify networking gaps.
Our objective based penetration test layers on and simulates an active attacker’s objective. This testing conducts a more advanced simulated cybersecurity attack. Object based penetration tackle specific tasks to reduce the risk of a breach.
This uncovers past or present threats like zero-day malware, trojans, ransomware, and other anomalies that may go unnoticed in standard automated vulnerability scans. It Identify any past breaches that may have gone undetected.
We offer robust protection against evolving cyber threats, safeguarding your digital assets and sensitive information. Our expert team employs cutting-edge
technologies, real-time monitoring, and proactive strategies to fortify your defenses. We assess vulnerabilities, implement stringent security protocols,
and provide swift incident response, ensuring your business stays resilient in the face of cyber attacks. Partner with us to create a secure digital
environment, so you can focus on your core operations without worrying about security breaches. Your trust, our commitment.
We offer robust protection against evolving cyber threats, safeguarding your digital assets and sensitive information. Our expert team employs cutting-edge technologies, real-time monitoring, and proactive strategies to fortify your defenses. We assess vulnerabilities, implement stringent security protocols, and provide swift incident response, ensuring your business stays resilient in the face of cyber attacks. Partner with us to create a secure digital environment, so you can focus on your core operations without worrying about security breaches. Your trust, our commitment to cybersecurity excellence.

In our comprehensive cybersecurity risk assessment, we start by identifying all digital assets, including hardware, software, and sensitive data. We assess vulnerabilities, analyzing potential threats and their impact on your organization. Through penetration testing and vulnerability scanning, we simulate real-world cyber attacks to evaluate your system's resilience. We evaluate existing security policies and procedures, ensuring compliance with industry standards and regulations. Detailed risk analysis helps prioritize threats based on likelihood and impact, guiding the development of a tailored security strategy. Our experts provide in-depth recommendations, empowering you to strengthen defenses, mitigate risks, and establish a proactive cybersecurity posture, safeguarding your business from potential threats in today's ever-evolving digital landscape.



Customized
Security
Advanced
technology
Protection
From threats
Proactive
Defense
Threat
Intelligence
Continuous
Improvement
Cybersecurity
experts
CYBERSECURITY
EXPERTS
CONTINUOUS
IMPROVEMENT
ADVANCED
TECHNOLOGY
PROACTIVE
DEFENSE
THREAT
INTELLIGENCE
PROTECTION
FROM THREATS
CUSTOMIZED
SECURITY
Our cybersecurity services offer robust protection for your digital assets. We provide 24/7 monitoring, threat detection, and incident response. Our
solutions are tailored to your unique needs, ensuring regulatory compliance, data privacy, and proactive defense. We safeguard your reputation
& financial well-being. Trust us for comprehensive, continuous security improvement in an ever-evolving digital landscape.
Our cybersecurity services offer robust protection for your digital assets. We provide 24/7 monitoring, threat detection, and incident response. Our solutions are tailored to your unique needs, ensuring regulatory compliance, data privacy, and proactive defense. We safeguard your reputation & financial well-being. Trust us for comprehensive, continuous security improvement in an ever-evolving digital landscape.








We are a team of experts who specialize in delivering top-notch website development, mobile app development, digital marketing, and custom software development services over the globe. Our team comprises highly skilled people who are committed to delivering quality work on time and within budget.
© 2024 Soft Enterprise. All Rights Reserved